Everything old is new again.
In Technology management we’re always pushing that boulder up the hill. At the same time, the hill is changing, our methods of pushing are changing, and our goals once we get to the top also change. The core IT function of protecting the network from intrusion has morphed and changed as the intruder’s methods have become more commoditized. For example: did you know you can now buy a “DDoS as a Service” package for as little as $5/month?
In the pre-pandemic network world, we could be content with traditional perimeter defenses. Sadly, relying on such security methods, with firewall and boundary scanning, is less effective and downright outdated. These network defenses epitomize the old Ronald Reagan/Cold War adage: “Trust, but Verify.” The internal network was trusted, as were all its users, and the verification was the user/password combination.
Now, where one’s office network includes countless new devices connecting from potentially insecure home networks, the old adage of Zero Trust network security has become the new norm. You could describe this approach as “Never Trust, Always Verify.”
In no particular order, here are the elements you need to undertake to protect yourself in this new world:
What are you responsible for?
You need to start with a complete inventory of all your devices: desktops, laptops, virtual desktop appliances, servers — everything that can fetch an IP address, and the credentials for each device. This is so you can determine if your users have Admin permissions to their own devices (BAD), if your MFP copier/printers have insecure default credentials and can be reached from outside the network, etc. etc. In IT Audit language, you’ve just determined your compliance visibility.
Users, Separated from their Jobs
It’s very helpful in large organizations to build “security containers” based not on individuals, but on job roles. The GP/AD accounts hold the permissions to various servers or resources, and the user particulars (email, phone, etc.) are swapped into those containers. This approach of simplifying granular user access controls allows access to specific information to follow the job, not the person. We HOPE that people will grow and change jobs within the company; we don’t necessarily want them to collect and retain all previous permissions. We used such an approach years ago at Blue Cross Blue Shield of Oklahoma, before they merged with IL/MN/NM/TX. Rest in Peace, John DeMint. It was time-consuming to set up but worth it in the long term.
Minimize your Attack Surface
Related to the section above, you want to provide your users the lowest level of access possible to perform their job’s essential functions. Virtual Desktop Infrastructure (VDI) appliances are great at this. By not having desktops that have multiple security layers, all users can have Standard access permissions to the virtual resource, and then onward from that we can determine exactly what Read/Write/Execute/Delete functions they need on all devices.
Reduce risk, complexity, and costs
One of the great things about the Zero Trust environment we’re setting up (in this the remote, cloud-based new world) is the ability to easily comb through vetted and auditable records and access requests. Microsoft365 has great capabilities in this regard, which makes the security manager’s role somewhat easier to find that needle in the haystack, which means fewer hours spent on those logs. Besides being able to ferret out strange network behaviors from outside, you’ll also see and be able to question strange behaviors from inside. Like when that user suddenly starts downloading voluminous files to his desktop or a thumb drive. You can then start to wonder if he/she is harvesting data prior to moving to a new job with a competitor…
Prevent lateral movement
You want to keep your users in their own areas. Segment your network by identity, VLAN, group, or function. This will keep hackers from freely traversing different parts of your network after they’ve gotten past your boundary defenses. Again, time-consuming to set up, but worthwhile.
Provide Layer 7 Threat Protection
The original Distributed Denial of Service (DDoS) attacks from the early 2000s until recently were so-called volumetric attacks: a whole boatload of compromised devices throwing Layer 3 or Layer 4 packets at hosts (websites generally) until they’re flooded and go down. These also overwhelmed the firewalls and routers that received those packets from the outside world, so it was a double-whammy to the organization.
The great Dave Dittrich formerly of the University of Washington taught many of us about DDoS via his deep examinations of malware that got in at the UW.
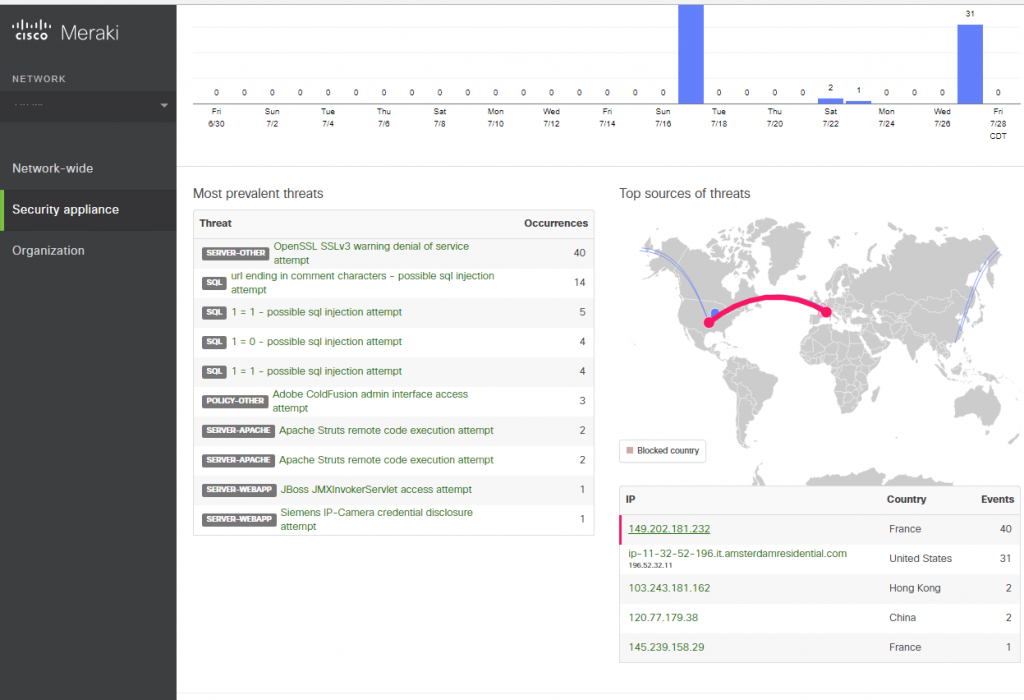
The new DDoS attacks are “low and slow” attacks: HTTP Floods that target the application layer. A single attack machine, suitably configured, can do great damage to a company’s web presence. See the pic above. Yes, if you have nefarious intent, you CAN buy access to such things. Keep your hands clean while your contractor does the dirty work.
The new and robust Layer 7 firewalls provide good defense against these, but only if you have an accurate profile of your normal web traffic. The point is to have regular snapshots over time of where your web visitors come from (when, how, what devices, etc.) so that when unusual fingerprints show up, you can block only those. I posted a pic not long ago of my ability to block all of France’s traffic for a bit while we looked in to some SQL Injection attempts. As an organization with no business relationship with anyone in France, it was a safe bet.
This is of course just the beginning. I’d be remiss not to mention the importance of Two-Factor Authentication, be it via cell text or 3rd-party apps: Authenticator, Authy, SecureID. There are many additional ways to layer redundancy in this new world. As the bad actors continue to find new approaches, we’ll continue to devise solutions and ways to keep our organizations safe.
[…] to mitigate or minimize damage before an attack happens. One set of approaches is described in my earlier post on Zero Trust security. The other is adopting an approach toward backups where you don’t rely on just ONE backup […]